Reversing the secret codes in the PatriotFront Leak
Plus the week's news, jobs, and events in security, privacy, and ethical tech
Feature story: Analyzing the PatriotFront leak

This month, activist group Unicorn Riot published a massive leak of chat logs from the white nationalist group Patriot Front. LaBac members have spent the past week analyzing the leak for better understanding of the inner workings of one of the more popular white nationalist groups in the US. Below are some of our findings.
Manifesto
For those unfamiliar with PatriotFront, you might start with their manifesto in their own words. This specific video of PatriotFront members reading their manifesto is currently going around on the internet, as members at one point remove their masks, and exclaim their support of Nazi ideology.

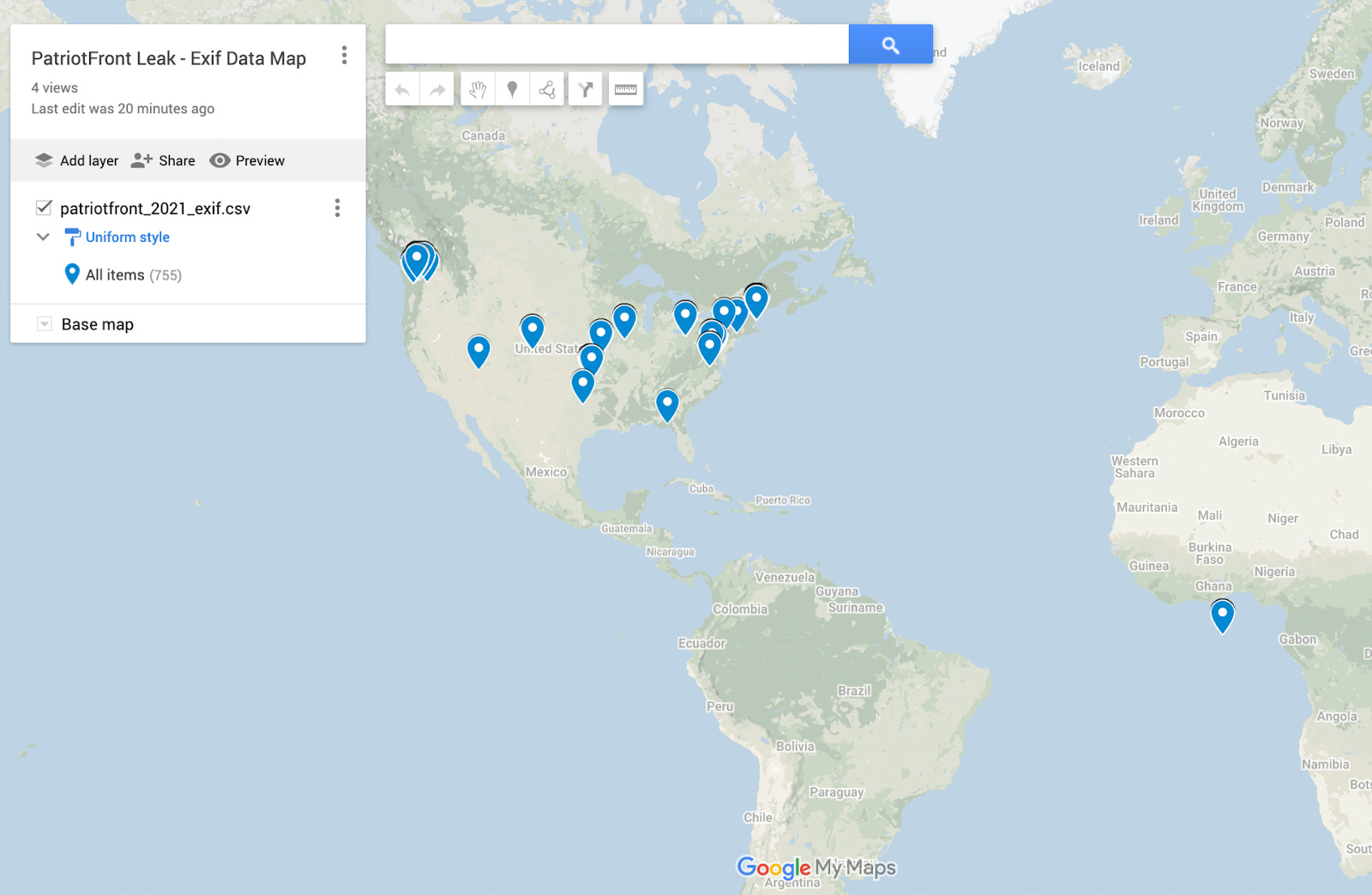
Extracting geolocation from PatriotFront media
A common open source intelligence technique when dealing with image media is to determine whether there is any attached EXIF data in the image metadata that may reveal the geolocation of where the picture was taken.
Some of PatriotFront’s most impactful operations are its “activism,” as it is referred to in the chat, involving the plastering of white nationalist propaganda in public places.
Where possible, LaBac members extracted the available EXIF data from media in the “activism” channel, where geolocation coordinates could then be placed on a map.
Secret codes in PatriotFront messages
Around the time that PatriotFront members discovered the leak, they referenced a formula and a “Python script” to decipher messages.
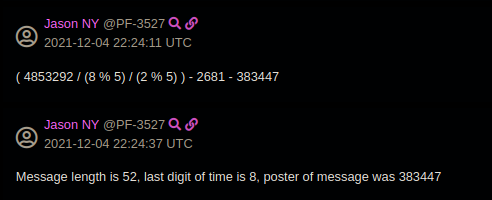
This formula makes use of the identifier given to users within RocketChat, the chat platform, as well as other identifying artifacts for a message.
The purpose of the formula seems to be to identify someone who might take a screenshot of a message by creating an identifier that can be mapped to a PatriotFront ID that members of the group are assigned internally.
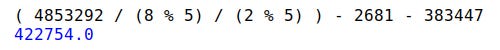
The result of the formula is the logged-in user's PatriotFront ID.
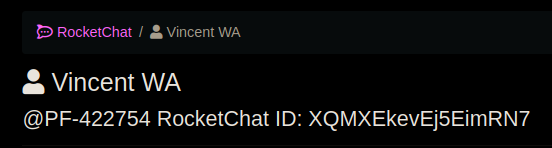
While this is a good method of finding infiltrators, they failed to implement any other security practices and didn't follow their own guidelines.
PatriotFront stored most of their photos documenting their activism in a central place, though at one point they set the #activism channel to delete older messages with a retention policy.
Selected charts from our PatriotFront leak analysis
Attendance sheet.
From the leak itself: an attendance sheet for PatriotFront members and their involvement in key meetings and trainings.

Key:
- M: Missed
- A: Attended
- P: Proxy
- AA: Attended with "Activism"
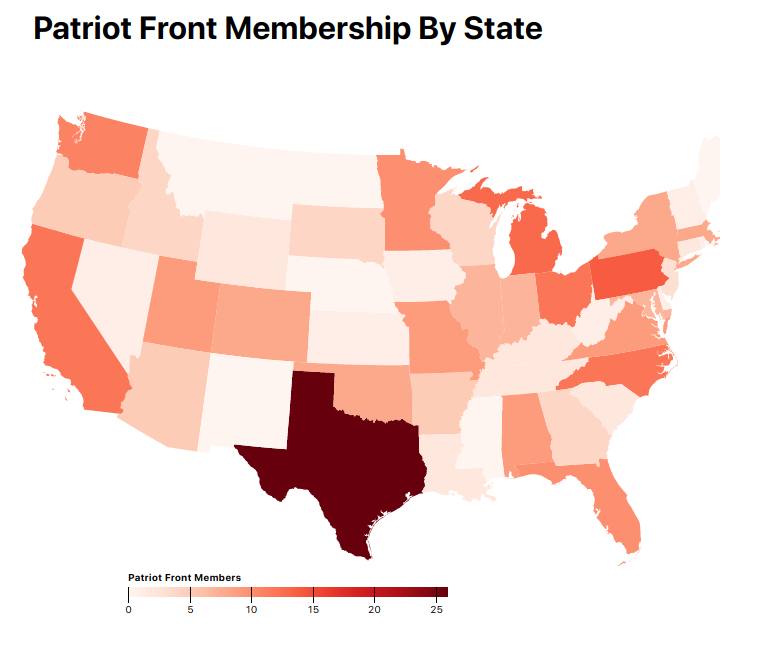
Statewide PatriotFront Membership
Heat graph depicting the volume of PatriotFront members per state.
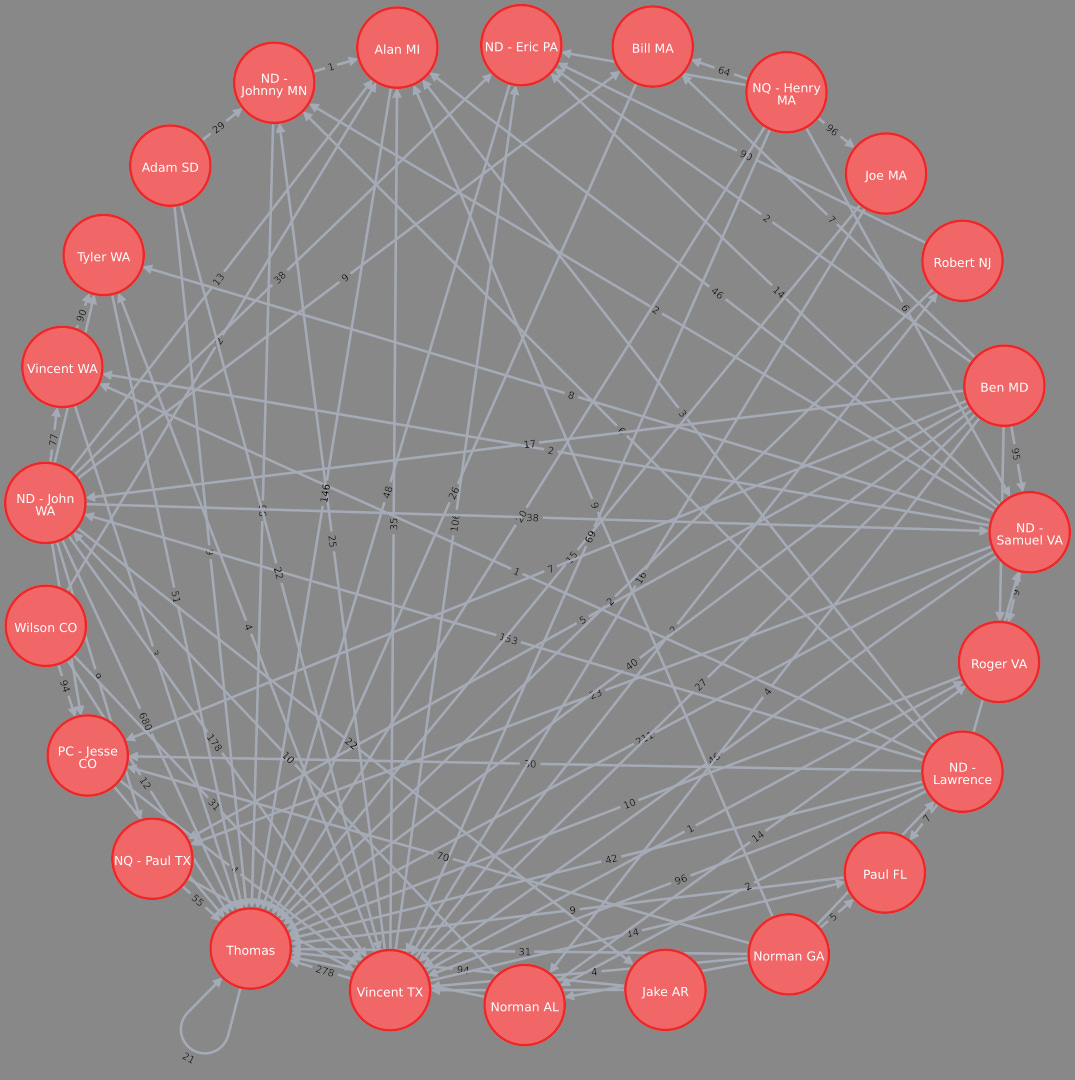
Most frequent chat sender/recipient pairs between PatriotFront members
Dependency graph depicting the most active PatriotFront members and their most popular recipients.
Special thanks to Emma and their team for their analysis.
News Roundup
TECH ETHICS AND PRIVACY
- [New Yorker] The blockchain business model has made headlines for sensational ploys. But in quieter corners DAOs are forging a promising new ecosystem for digital startups.
- [Politico] The Crisis Text Line’s AI-driven chat service has gathered troves of data from its conversations with people suffering life’s toughest situations. Politico reveals Crisis Text Line shares that data with a for-profit offshoot.
- [The Markup] Life360 Says It Will Stop Selling Precise Location Data. Announcement comes after The Markup identified the family tracking app as one of the largest sources of raw data for the location data industry.
TECH LABOR EVOLVING
- [Economist] Citizen developers are rapidly becoming the vanguard of corporate digitization.
- [Financial Times] Amazon abandons influence campaign designed to attract staff. Paying warehouse workers to tweet positive comments is dropped after poor reach and embarrassing backfires.
- [Vice] “Amazon Paid for a High School Course. Here’s What It Teaches.”
HACKING AND SECURITY INCIDENTS
- [Bloomberg] Hackers Seize $80 Million From Qubit in Latest DeFi Attack.
- [Ars Technica] Microsoft fends off record-breaking 3.47Tbps DDoS attack.
- [Ars Technica] A bug lurking for 12 years gives attackers root on most major Linux distros.
- [Pradeo] Malicious app on Google Play drops banking malware on users’ devices.
- [Crowdstrike] This blog discusses the StellarParticle campaign and the novel tactics and techniques used in supply chain attacks observed by CrowdStrike incident responders.
SECURITY TRENDS AND ANALYSIS
- [New York Times] A Times investigation reveals how Israel reaped diplomatic gains around the world from NSO’s Pegasus spyware — a tool America itself purchased but is now trying to ban.
- [Sentinel One] Hacktivism and State-Sponsored Knock-Offs: Attributing Deceptive Hack-and-Leak Operations.
- [The Verge] In the ’80s, Susan Headley ran with the best of them—phone phreakers, social engineers, and the most notorious computer hackers of the era. Then she disappeared.
COOL STUFF ON OUR RADAR
- [Nex] Friend of cabal and master NSO Pegasus hunter Nex gives a primer on Android forensics.
- [@_alialkhatib on Twitter] “talk to your kids about... uploading precise three-dimensional scans of their bedrooms to the whole wide world.”
- [Space Raccoon] Applying Offensive Reverse Engineering to Facebook Gameroom.
- [@kevinbacker on Twitter] “Even if your model/algorithm/tool generates good predictions, it might not generate trust, credibility, political organization or political will. Those are the most important questions and they are almost always neglected.”
- [@Zerodium on Twitter] Zerodium ups the bounty for zero-day vulnerabilities in Mozilla Thunderbird and Microsoft Outlook.
Jobs & Other Opportunities
Policy Analyst - Knight First Amendment Institute, Columbia University
The ideal candidate will have an interest in and familiarity with issues at the intersection of free speech and technology, experience in policy analysis and policy strategy and advocacy. [Knight Center]
Senior Product Designer, Plan - GitLab
As a Senior Product Designer at GitLab, you will work 1:1 with a Product Manager and be embedded in our Plan: Project Management team. You'll design features for our highly-visible planning and planning analytics capabilities that empower small, autonomous teams. [GitLab]
Senior Cybersecurity Engineer - Rigetti Quantum Computing
As our 1st Security Engineering hire, you champion the intersection of technology, process, and people to be the conduit for Rigetti in sharing our cutting edge technology with the rest of the world. [Rigetti]
Events
Startup Chica
Saturday, February 26th 2022 from 10:00 AM CST to 5:00 PM CST
The Startup Chica Conference focuses on teaching, inspiring and encouraging young females to enter the business world by becoming leaders and entrepreneurs while fostering their ideas and talents.
Threat Modeling - Intensive Course
February 28 - March 4th, 8AM-10AM Pacific.
Equivalent to a 2 day in-person course. Participants will deepen knowledge & skills needed to consistently and efficiently utilize threat modeling to identify threats, mitigation techniques, document results, deliver more secure products, and champion threat modeling within organizations.
