A Look at Two ‘Hackers’ Propagating Disinformation Narratives
Newsletter and intel from the LaBac Hacker Collective


Citizen reporting comes in all shapes and sizes and this week there's a number of self-styled investigators (read: mid-level sophistication shitheads) that are leveraging their shallow knowledge of technology to come to wild conclusions that support a pre-conceived falsehood — namely, the false story that the Democrats have somehow rigged the 2020 presidential election.
Earlier this week, two individuals set out to use their technical skills to disclose potentially damaging information, all with the goal of fitting this broader “stolen vote” disinformation narrative.
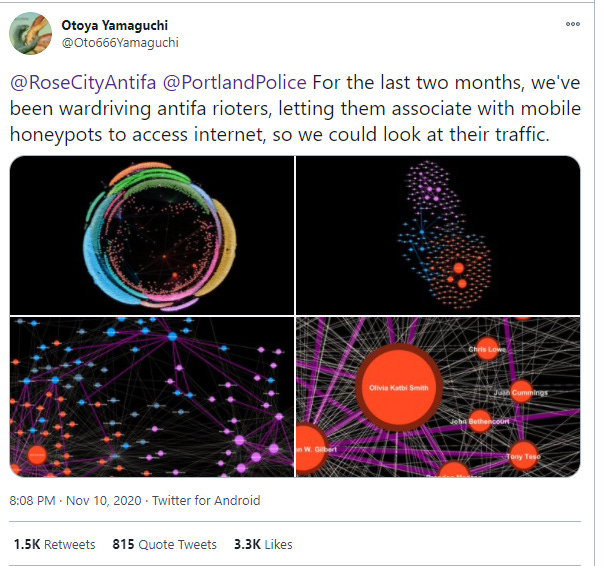
In one Twitter thread, @Oto666Yamaguchi (now suspended) claimed to have collected cell phone data on “antifa” in an effort to dox them. And in another Twitter thread, @We_Have_Risen claimed they were able to show reverse engineering of voting machine software from Dominion Systems, the election operations company.
In the first example, we have a user claiming to be leveraging femtocell tech to identify individuals in a protest. If they actually had a femtocell this is probably the least interesting thing they could do with that technology (so we call bull). Our guess is what they’re actually doing is running a fake wireless access point (also affectionately known as WAP … so a fake WAP if you will) and stripping information from Twitter page loads. Even if their data is accurate, a perceptive reader will note that it only yields information they already knew about the protest. There's nothing tying the named actors to those locations…
In the second thread, Twitter user @We_Have_Risen claims to be reverse engineering Dominion Systems’ “Democracy Voter Suite” software. The analysis is rife with implications and assumptions that, of course, lead to the disinformation narrative that the 2020 election was rigged by Democrats.
It appears the decompilation of the software is remarkably well put together, but there are peculiarities with what has been posted in the tweets. For one thing, the code has comments and named classes methods and objects. If the software was actually decompiled like the user claims, the resulting code wouldn't have any of the details resembling the structures posted in the tweets.
So does @We_Have_Risen “have the source code” like they claimed earlier, or is this just another attempt (albeit a more technical one) to demonstrate an increasingly disproved narrative?

Fighting Surveillance Tech with Trademark Transparency (Friday, November 20 - 5pm EST) - Decoding Stigma is holding a workshop about trademarks and copyrights applied to personal images, with implications for facial recognition, sex work and sexually exploitative material. [Eventbrite]
Rise of the Robots: Challenging automated decision-making in government (Wednesday, November 17-19 - 7pm EST) - This conference is designed to equip public lawyers with the practical knowledge and skills required to challenge automated government decisions. [Public Law Project]
How Technology Can Shape the COVID-19 Recovery for Racial and Gender Equity (Wednesday, November 18 - 7pm EST) - The founder of community tech group Silicon Harlem is a panelist in this fundraising event for NYC Councilmember Kallos. [Kallos NYC]
Book Launch: Predict and Surveil by Sarah Brayne (Friday, November 20 - 3pm EST) -Discussion of Sarah Brayne's new book Predict and Surveil: Data, Discretion, and the Future of Policing. [RSVP]

Election Violence and Digital Misinformation
- [The Hill] [New York Times] On Tuesday, federal authorities arrested Staten Island resident Brian Maiorana for making death threats against protesters, politicians, and police, including threats directed at Senate minority leader Chuck Schumer. Maiorana had posted the threats on social media.
- [abc News] Last Thursday, police arrested Larry Krasner and Joshua Macias, both from Virginia, outside the Philadelphia Convention Center for carrying firearms without licenses. A spokesperson for the Philadelphia District’s Attorney's Office later said that the men believed fake ballots were being counted at the center.
- [Reuters] Katie Paul (@katielpaul) reports that last week members of right-wing Facebook groups called for armed violence in the case that Trump lost the presidency. Digital intelligence firm Counter Action found that similar violent rhetoric was not uncommon in the lead up to the election.
- [Mother Jones] Last Thursday, Ali Breland (@alibreland) reported that one massive Facebook group, “Stop the Steal”, which accuses Democrats of election fraud has ties to Republican operatives, including Liberty Lab, a digital media firm with conservative clients.
- [CNN] CNN is collecting all their coverage on misinformation, disinformation, and other fact-checking resources on this single portal. So far, they’ve tallied over 74 detailed posts concerning prominent misinformation news since mid-October.
More Reads at the Nexus of Big Tech and Politics
- [Mashable] A critical deplatforming: PayPal has cut ties with several far-right and white nationalist groups, including the Proud Boys and David Duke. Such a direct disruption of these groups’ funding sources has them mad!
- [Reuters] As the Biden transition team begins to pick their selections for various offices and policies, it is clear that the President Elect’s moderate political nature will impact progressive tech legislation. Almost all the candidates for the President-Elect’s tech policy team are Big Tech alumni, as opposed to those who study the industry critically.
- [MIT Technology Review] Shorenstein Center Research Director Joan Donovan (@BostonJoan) takes a closer look at how right-wing operatives are using and spreading “riot porn” to shape public perception and mobilize white vigilante groups.
- [Vox] Bizarre, yet disturbingly reflective: How the internet uncovered that the social media account of a pro-Trump “gay Black man” led to Dean Browning — a white, small-town Pennsylvania politician — at a time when tech companies continue to struggle with the pervasive problem of digital blackface.
On Our Radar…
- [Wired] On Nov. 3, the Department of Justice seized nearly $1 billion in Bitcoin with cooperation from an unidentified hacker. The cryptocurrency had originally belonged to Ross Ulbricht, who amassed the amount while running the Silk Road, but it was missing from Ulbricht’s assets when he was initially arrested.
- [The New York Times] A deep-dive profile on Hasan Piker, who has found a winning combination of video game streaming platform Twitch and progressive politics.
- [FiveThirtyEight] Political scientist Lee Drutman (@leedrutman) conducts a historical and data-informed analysis to illuminate the reasons behind the current vitriol in politics.
- [Google] The team behind Google’s open source initiatives lay out their vision for a more inclusive engineering discourse.

Hate speech website: ar15[.]com
Who hosts: Amazon Web Services
Today’s site is ar15[.]com. While the site hosts seemingly normal content and media about firearms, the forums of the site are teeming with sexism, bigotry, and conspiracies.
ar15[.]com uses Amazon Web Services to host their infrastructure. Since the site seems to use several AWS solutions and content delivery services, their network and infrastructure may change often, but we have previously observed the site with the IP 3.12.159[.]24.
